VMware deprecated the old NSX-T 3 way of setting SSL Certificates for the Management Cluster using the cluster/api-certificate API-Call. With NSX-T 4 onwards you will have to use the trust-management API.
Add a Certificate for the Cluster to use
First, you will need to create a Certificate Signing Request containing all FQDNs of the Manager-Nodes as well as the designated FQDN for the cluster’s VIP. Add all the FQDNs in the Common Name, as well as the Subject Alternative Name fields. A tool I like to use for demonstration purposes is the certificatetools.com online generator: CertificateTools.com – Online X509 Certificate Generator
While a seemingly reliable source, keep in mind that the site could store your Private Key for the certificate. I the certificate gets published, the site could use your public certificate and the stored key for malicious purposes. Always generate a CSR in a trusted environment for production purposes.
Add the Certificate Chain and the private Key to NSX
To add the certificate to the NSX-Management-Cluster, navigate to “System” > ” Settings” / “Certificates” in Policy-mode.
Then, simply select the “Import” > “Certificate” option and paste the Base64-encoded certificate contents of the certificate and the corresponding private key in the appropriate field. Be sure to set the “Service Certificate” switch to “No”, as else you will not be able to use the certificate for management purposes as it will be reserved for Load Balancers, etc.
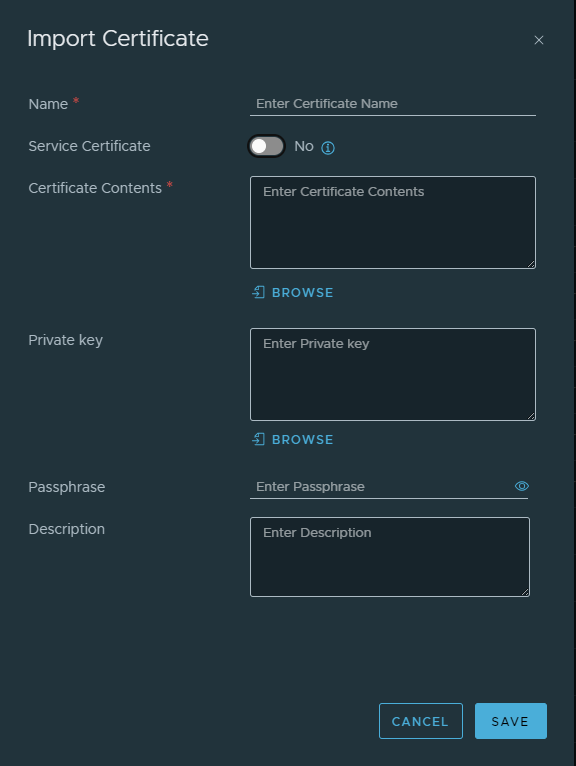
When the certificate is imported, expand the correct entry in the list down below and note down the “ID” value displayed.
Validate and set the certificate
For the next part you will need to make some API calls. For all things API I like to use a tool like postman as it visualizes the tasks performed in a nice way, but using CURL or Invoke-WebRequest will also work fine.
You will have to use basic authentication with a privileged user.
The first API call will verify the certificates validity and check if it fits for our designated use as a Management-Cluster certificate. Replace the values under NSX_IQ_FQDN and CERTIFICATE_ID with the NSX-VIP or Manager-IPs and the in NSX displayed ID for the certificate:
https:// NSX_IP_FQDN /api/v1/trust-management/certificates/ CERTIFICATE_ID ?action=validateFor a successful validation, expect the following output with a HTTP status code of 200:
{
"status": "OK"
}If everything is well, you can apply the certificate to the Management-Cluster:
https:// NSX_IP_FQDN /api/v1/trust-management/certificates/ CERTIFICATE_ID ?action=apply_certificate&service_type=MGMT_CLUSTERThis command will only result in a HTTP status code of 200. If this is the case, wait for approximately 5 minutes, delete your cache and the NSX-Manager should use the new certificate.
Update the API Host Certificate
When this is done, you can also update the API Certificate, which will be used when connection to the NSX API service. You will also need to provide each Node-IDs for this call and will have to execute it for each Management-Cluster node. Replace the corresponding values. The quickest way to get the Node-IDs in use, just execute the call without a Node-ID-value, the call will fail and output the Node-IDs in use.
https:// NSX_IP_FQDN /api/v1/trust-management/certificates/ CERTIFICATE_ID ?action=apply_certificate&service_type=API&node_id= NODE_ID